Archive for September, 2020
Zero Trust approach
We talk a lot about security and protecting ourselves from external threats, threats started to emerge from inside your enterprise fence, hence protecting your business assets became a necessity. The question we hear a lot now is how do we protect our business? The answer is by embracing the “Zero Trust model”.
So, what is “Zero Trust model”? I hear you say! It is a set of rules and principles that dictates the way we should look at our identity, network/data and infrastructure security, and devices (both corporate and with companies implementing BYOD).
Lets look at those principles in more detail and define a simple strategy in setting our goal for more secure environment without impeding productivity.
Identity – people when they hear identity they think of two-factor authentication straight away, problem solved! or is it? Unfortunately, it’s not as simple as implementing 2FA or multi-factor authentication (MFA), it’s about knowing who, what, where and which:
Who – who are you in the context of a username and password, a lot of business are going passwordless (i.e. bio-metrics)
What – what device are you using to access, does the device comply with company policy (such as patches, anti-virus etc)
Where – where are you accessing from (i.e. geo location), are there any anomalies, such as login attempt from distant geo locations in a short period of time.
Which – which service/data are you trying to access, so having appropriate permissions set is a key, using least privilege as the base for applying permissions. Not to forget auditing those permissions and their access is also a must to ensure access is being evaluated appropriately.
There are many factors that need to be surfaced in order for the IT department to be able to understand how their staff are authenticating and being authorised to access corporate data or service.
As we discussed earlier that businesses are facing a lot of threats not just from external sources but internal ones as well, including rouge admins (whom hold the key to the kingdom!). Implementing identity management is important in the era of cyber wars, having services such as Azure AD that integrates and compliments your on premise AD enables you to detect and prevent suspicious logon’s by taking all the above into consideration.
Azure AD uses Machine Learning in the core to look at billions of signals received to learn and detect anomalies, conditional access would also complement this solution, through understanding the context and risks of sing ins and provide the right access.
How can you start protecting yourself?
Identity management life-cycle management is a key topic, policies to enforce strong passwords but also making it easier for users to remember them without the need to write them on a sticky note and leave them on their laptop, or even better
The use of multi-factor authentication, so just a password isnt enough anymore. How can I verify my staff identities? With something they are (i.e. username), something they remember (i.e. password) and something they have (i.e. phone or physical token).
Some of the points above might not be news to you, but ensuring appropriate policies are in place with audit trail and appropriate assessment of access is a must, through assume breach approach.
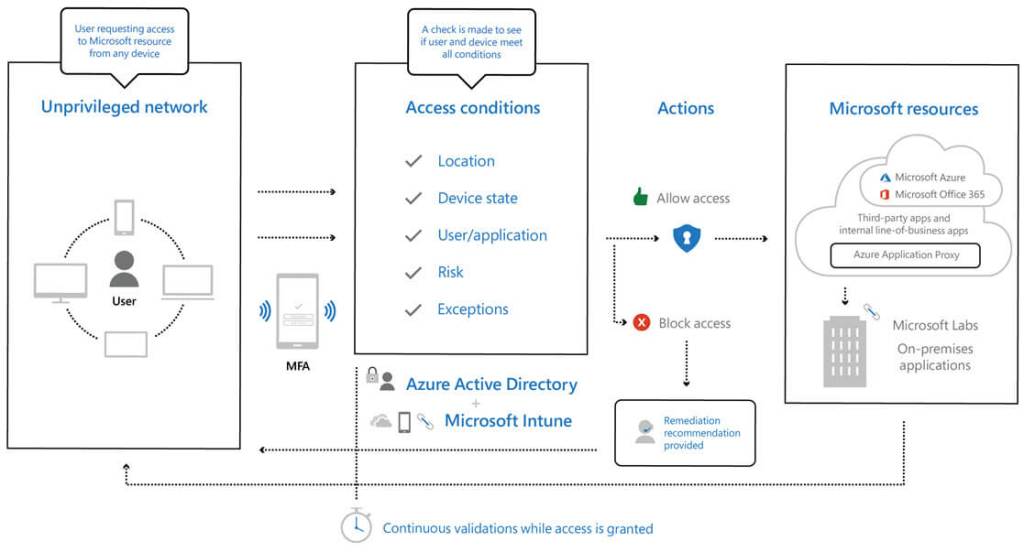
The high level architecture above shows level of security taken by corporations such as Microsoft to secure their assets and services, Microsoft doesnt take it lightly when it comes to security, it’s the heart of their service of which Microsoft Azure, Microsoft 365 and Dynamics 365 are built.
As shown through the simplistic architecture above, the extensive use of Azure AD services such as MFA, Conditional access, in addition to enrolling devices into Microsoft Intune to manage device health would ensure that access is traced and authorised appropriately. This approach would provide a cloud scale and an enterprise grade service.
Its important now days to minimise the blast radius when it comes to a compromise, by minimising lateral movements through the appropriate use of network segmentation, using encryption through all user access sessions and between different tiers, in addition to using analytics to get visibility and drive threat detection and improve defences such as Azure Sentinel.
Using this as the core topic for our next discussions, by building security and zero trust model in the core of our design offerings.